Improving Digital Banking Security: Two-Factor Authentication

Digital banking has changed how we manage money. With just a few taps, users can transfer funds, pay bills, and check balances from anywhere in the world. However, this convenience comes with risks. As banking moves online, it also becomes a prime target for hackers and scammers, prompting banks to adopt advanced security measures to protect their customers.
The Problem: Security Risks in Digital Banking
While digital banking has made transactions faster and more accessible, it has also created opportunities for digital threats. Hackers and scammers can strike from anywhere, using techniques like phishing, malware, and identity theft to compromise user accounts.
To tackle these challenges, banks have implemented various security measures, such as:
SMS Verification: Sending one-time codes via text messages to verify identity.
Geolocation Tracking: Using location data to detect suspicious logins.
Two-Factor Authentication (2FA): Requiring a second verification step alongside passwords.
Single-App Sign-Ins: Restricting access to one device at a time to prevent unauthorized access.

The Importance of Two-Factor Authentication (2FA)
2FAs are crucial for securing digital banking. It adds a second layer of verification, making it harder for attackers to gain access even if they have the password. Its provides several key benefits:
Enhanced Security: Even if a password is compromised, the attacker would need the second key (a code or physical device) to access the account.
Mitigation of Phishing Attacks: Even if users unknowingly share their password, the absence of the second factor prevents unauthorized access.
Increased User Confidence: Knowing their accounts are protected by an extra layer of security reassures users.

Current 2FA Methods and Their Issues
SMS Verification
A one-time password (OTP) is sent to the user’s phone number, which is needed to complete the login.
Advantages: It’s simple and requires no additional devices.
Challenges: SMS codes can be intercepted by malware or SIM-swapping attacks.
Physical Tokens
Physical tokens, such as key fobs, generate unique codes for authentication.
Advantages: They are independent of the internet and phones, making them harder to compromise.
Challenges: Tokens are costly to produce and distribute. Users find it inconvenient, who find carrying an extra device cumbersome.
App Authenticators
Apps like Google Authenticator provide one-time passwords for 2FA.
Advantages: They are more secure than SMS and don’t rely on mobile carriers.
Challenges: Setting up and managing these apps can be confusing for some users, and losing access to the app can cause lockouts.
"How might we make two-factor authentication both more secure and seamless, while improving their overall experience?"
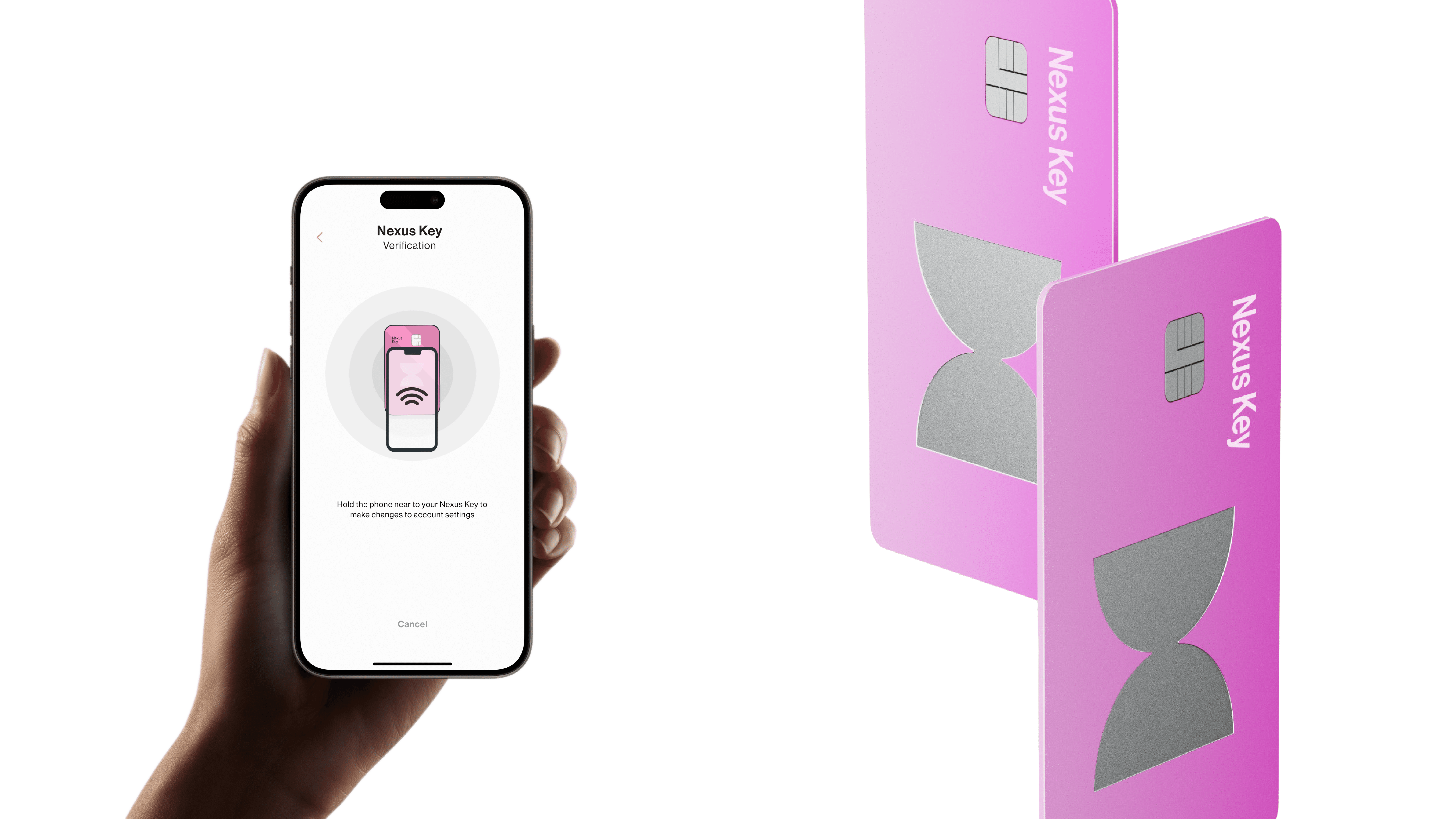
The Idea: NFC-Enabled Two-Factor Authentication
Phones come equipped with NFC (Near-Field Communication) technology, which enables devices to communicate by simply being in close proximity. This presents a clear opportunity to enhance two-factor authentication (2FA), making it both more secure and seamless.
Smartphones already use NFC for contactless payments, why not harness the same technology to protect banking accounts and secure transactions?
NFC Cards as Keys: A Technical Feasibility Study
In banking, convenience and security are often at odds. Users want seamless interactions, but stringent security measures can sometimes feel cumbersome and confusing.
Near Field Communication (NFC) technology offers a possible solution that balances these needs. This case study explores the feasibility of using NFC cards as keys in digital banking, highlighting their potential to enhance security and simplify user interactions while addressing common pain points in authentication and access control.
Making sure the idea work
When designing solutions, we must also ensure that the technology can be implemented. In this case, the idea is to use NFC cards as keys for signing into mobile applications, providing users with a secure, contactless authentication method.
Thus we evaluated the viability of NFC technology is a viable option by analyzing its technical, security, and user experience aspects.
What Is NFC and How Does It Work?
NFC is a short-range wireless communication technology that allows devices to exchange data when they are close. It’s widely used in contactless payments (Google Pay, Apple Pay, &c), key cards, and even in home automation.
Key Cards: Many offices and hotels use NFC-enabled ID cards to unlock doors.
Smart Locks: Devices like Samsung’s SmartThings Hub let users unlock doors with an NFC card or smartphone.
Automotive: Tesla’s NFC key cards serve as backup keys for its vehicles.

Feasibility Analysis
Technical Feasibility
Modern smartphones support NFC, allowing them to interact with NFC cards. This means users can take advantage of NFC features without needing extra gadgets, making the technology accessible and easy to use for everyday tasks like digital banking or access control.
Users having banking cards tied to their accounts, and they can also serve as a secure authentication tools. These cards can provide an additional layer of security while remaining cost-effective for banks. This approach allows banks to leverage existing infrastructure while enhancing both convenience and security for their customers.

Security Feasibility
NFC cards are both easy to use and secure, making them a great option for tasks like digital banking. They ensure safety through several key features:
Rolling Keys
NFC cards use a security method called rolling keys to keep your information secure. Every time you tap your NFC card, it generates a new, one-time-use code that is different from the last one. This means even if someone manages to see the code during the interaction, it won’t work again.
Proximity Authentication
NFC communication requires close proximity, minimizing the risk of unauthorized interception.
Encryption
Data transmitted between the NFC card and the reader is encrypted using algorithms like AES-128. This ensures that sensitive information cannot be easily intercepted or decoded. Many NFC cards are equipped with tamper-resistant chips that prevent cloning or data extraction, ensuring the integrity of the stored data.
Market Feasibility
Market trends shows strong user familiarity with NFC , thanks to its prevalence in contactless payments and public transit systems. Competitors like YubiKey and Tesla’s NFC key cards have demonstrated a growing demand for NFC-based solutions in security and access control.
Conclusion
NFC cards present a secure, user-friendly, and cost-effective solution for authentication and access control. Their ability to generate rolling keys, encrypt data, and work in close proximity ensures robust security, while their simplicity improves user experience. For UI/UX designers and product developers, NFC technology offers exciting possibilities for creating seamless, secure interactions.
It’s clear that integrating NFC cards as a 2FA method is not only practical but also offers exciting possibilities for creating seamless, secure interactions.
BENJAMIN TAN DE JUN
©2024 Elemental Grey Studio. All rights reserved.